"Security Connection Failed" when connecting to IIS web server over HTTPS that only has TLS 1.2 enabled
Using Firefox 62.0.2 in Windows 10. Trying to connect to our IIS webserver that only has TLS 1.2 enabled but encounter the following error:
"Secure Connection Failed. The connection to the sever was reset while the page was loading"
If I enabled TLS 1.1, TLS 1.0 on the server, the connection via TLS 1.2 works fine. Chrome and IE browser don't have this issue and can connect when TLS 1.2 is exclusively enabled.
Our security group frowns on enabling TLS 1.1 / TLS 1.0. Please advise on how to get TLS 1.2 (exclusive) working with latest Firefox for Windows 10.
Opaite Mbohovái (20)
What version of IIS server you use? It's TLS 1.2 enabled on your server? On the other side this error may occur due to a certificate issue. It's your certificate ok ? (configuration, validity, authority) You can verify it at: https://www.ssllabs.com/ Hope this help!
IIS 7.5
Cert is fine in Chrome / IE, not Firefox.
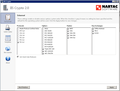
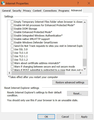
Attaching screen shot of TLS configuration on server that causes HTTPS connection error in Firefox.
Try this Firefox
1. In the address bar, type “about:config” and hit enter.
2. In the “Search” field, enter TLS. Find and double-click the entry for "security.tls.version.min"
3. Set the integer value to “2” to force a minimum protocol of TLS 1.1 (entering "3" would force TLS 1.2).
4. This configuration will now show the new value and will take effect immediately (don’t forget to clear your cache).
Hope this help! Let's me know if work!
old (Secure Connection Failed) security.tls.min = 1 security.tls.max = 4
new (Secure Connection Failed) security.tls.min = 3 security.tls.max = 4
But what happened if you maintain TLS 1.1 not 1.0? (change min to 2 check 1.1) just a suggestion Another idea: On windows search Internet Options Click advanced and disable TL1.0 1.1
Moambuepyre
Disabled TLS 1.0 / TLS 1.1 in Internet Options / Advanced. Still can't connect over HTTPS. Does Firefox have any advanced logging that will log the TLS handshake?
Wow, that Nartac software looks really interesting.
So if I set Firefox to use ONLY TLS 1.2 and then use the following test page --
https://www.ssllabs.com/ssltest/viewMyClient.html
-- I get the following list of ciphers. It's hard to match up with the Nartac screenshot. Some parts seem obvious, but other parts aren't (ECDH vs. ECDHE key exchange the same? the third part of the block cipher, CBC/GCM?).
Cipher Suites (in order of preference) TLS_ECDHE_ECDSA_WITH_AES_128_GCM_SHA256 (0xc02b) TLS_ECDHE_RSA_WITH_AES_128_GCM_SHA256 (0xc02f) TLS_ECDHE_ECDSA_WITH_CHACHA20_POLY1305_SHA256 (0xcca9) TLS_ECDHE_RSA_WITH_CHACHA20_POLY1305_SHA256 (0xcca8) TLS_ECDHE_ECDSA_WITH_AES_256_GCM_SHA384 (0xc02c) TLS_ECDHE_RSA_WITH_AES_256_GCM_SHA384 (0xc030) TLS_ECDHE_ECDSA_WITH_AES_256_CBC_SHA (0xc00a) TLS_ECDHE_ECDSA_WITH_AES_128_CBC_SHA (0xc009) TLS_ECDHE_RSA_WITH_AES_128_CBC_SHA (0xc013) TLS_ECDHE_RSA_WITH_AES_256_CBC_SHA (0xc014) TLS_RSA_WITH_AES_128_CBC_SHA (0x2f) WEAK TLS_RSA_WITH_AES_256_CBC_SHA (0x35) WEAK TLS_RSA_WITH_3DES_EDE_CBC_SHA (0xa) WEAK
What would be helpful is if you could get IIS/Nartac to display a list of the acceptable ciphers with all the bits and pieces assembled in a similar format rather than with individual checkboxes, since some of those might not actually be compatible/combined with one another.
The https://www.ssllabs.com/ssltest/ tool does that, but it probably can't run against internal servers because it's a webapp.
As a point of reference, what cipher do other browsers use when connecting to the site?
Try to disable MD5 and SHA Disable Null cipher if enabled
Turned off MD5 and SHA on the server and tried again to connect via HTTPS on client : "Secure Connection Failed"
However, I did run fiddler this time and capture the following trace:
A SSLv3-compatible ClientHello handshake was found. Fiddler extracted the parameters below.
Version: 3.3 (TLS/1.2) Random: 23 80 F2 C9 F9 B8 00 1F A3 2D B4 19 C5 6F 24 FC 20 75 55 23 6E 6B 6A E4 20 98 E6 8F 16 C0 C6 F0 "Time": 5/13/2077 1:28:51 AM SessionID: 7D FD EF B8 B1 69 69 88 2B 58 0C 25 EA 59 7D 79 99 0E 63 86 F4 5F C9 AD CD 65 4B DA F0 B0 76 66 Extensions: server_name devworkflowweb.foo.com extended_master_secret empty renegotiation_info 00 elliptic_curves unknown [0x1D), secp256r1 [0x17], secp384r1 [0x18], secp521r1 [0x19], unknown [0x100), unknown [0x101) ec_point_formats uncompressed [0x0] SessionTicket empty ALPN h2, http/1.1 status_request OCSP - Implicit Responder 0x0033 00 69 00 1D 00 20 F5 9D 57 58 8F 9E 6C BE 55 0D AC 40 AC A3 F2 BA 9B 0B BF A2 D4 77 7C 60 98 80 BD 98 0B 3E 13 63 00 17 00 41 04 CF 9E AB E7 70 C3 CE AB 08 7D E0 AA 6A B3 7F E9 32 14 E1 A1 EF 03 EC 4F 0E F9 72 8B D1 7E 28 3E BE 65 0D 7A 50 EF 27 C3 64 1E A6 3D 2E 0B 71 9C 00 59 0C 44 11 BD 2A 0B 32 81 CD 25 4E 70 92 A0 0x002b 04 7F 1C 03 03 signature_algs sha256_ecdsa, sha384_ecdsa, sha512_ecdsa, Unknown[0x8]_Unknown[0x4], Unknown[0x8]_Unknown[0x5], Unknown[0x8]_Unknown[0x6], sha256_rsa, sha384_rsa, sha512_rsa, sha1_ecdsa, sha1_rsa 0x002d 01 01 0x001c 40 01 padding 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 Ciphers: [1301] Unrecognized cipher - See http://www.iana.org/assignments/tls-parameters/ [1303] Unrecognized cipher - See http://www.iana.org/assignments/tls-parameters/ [1302] Unrecognized cipher - See http://www.iana.org/assignments/tls-parameters/ [C02B] TLS_ECDHE_ECDSA_WITH_AES_128_GCM_SHA256 [C02F] TLS_ECDHE_RSA_WITH_AES_128_GCM_SHA256 [CCA9] TLS_ECDHE_ECDSA_WITH_CHACHA20_POLY1305_SHA256 [CCA8] TLS_ECDHE_RSA_WITH_CHACHA20_POLY1305_SHA256 [C02C] TLS_ECDHE_ECDSA_WITH_AES_256_GCM_SHA384 [C030] TLS_ECDHE_RSA_WITH_AES_256_GCM_SHA384 [C00A] TLS1_CK_ECDHE_ECDSA_WITH_AES_256_CBC_SHA [C009] TLS1_CK_ECDHE_ECDSA_WITH_AES_128_CBC_SHA [C013] TLS1_CK_ECDHE_RSA_WITH_AES_128_CBC_SHA [C014] TLS1_CK_ECDHE_RSA_WITH_AES_256_CBC_SHA [0033] TLS_DHE_RSA_WITH_AES_128_SHA [0039] TLS_DHE_RSA_WITH_AES_256_SHA [002F] TLS_RSA_AES_128_SHA [0035] TLS_RSA_AES_256_SHA [000A] SSL_RSA_WITH_3DES_EDE_SHA
Compression: [00] NO_COMPRESSION
signature_algs sha256_ecdsa, sha384_ecdsa, sha512_ecdsa, Unknown[0x8]_Unknown[0x4], Unknown[0x8]_Unknown[0x5], Unknown[0x8]_Unknown[0x6], sha256_rsa, sha384_rsa, sha512_rsa, sha1_ecdsa, sha1_rsa
you disabled md5 Is considered not secure But your certificate use md5 signature? If yes here could be the problem. you say Cert is fine in Chrome / IE, not Firefox. when you capture traffic of a successful connection what fiddler capture?
hope this help
Moambuepyre
when you have a successful connection what fiddler capture? Try to compare
Moambuepyre
Does the server respond with its preferred set of ciphers? Maybe not with Firefox but with another browser...
Using HTTPS / TLS 1.2 exclusive, I connected to the same server with IE 11. Here is the fiddler dump:
A SSLv3-compatible ClientHello handshake was found. Fiddler extracted the parameters below.
Version: 3.3 (TLS/1.2) Random: 5B B6 2F E9 08 9F F2 25 6E FC B0 76 16 F0 50 06 04 9C B8 BF 8C 8D 0B 80 C4 B1 C5 BF 65 EA CD 29 "Time": 12/21/2093 1:16:43 AM SessionID: empty Extensions: server_name devworkflowweb.foo.com status_request OCSP - Implicit Responder elliptic_curves unknown [0x1D), secp256r1 [0x17], secp384r1 [0x18] ec_point_formats uncompressed [0x0] signature_algs sha256_rsa, sha384_rsa, sha1_rsa, sha256_ecdsa, sha384_ecdsa, sha1_ecdsa, sha1_dsa, sha512_rsa, sha512_ecdsa SessionTicket empty ALPN h2, http/1.1 extended_master_secret empty 0x0018 00 10 03 02 01 00 renegotiation_info 00 Ciphers: [C02C] TLS_ECDHE_ECDSA_WITH_AES_256_GCM_SHA384 [C02B] TLS_ECDHE_ECDSA_WITH_AES_128_GCM_SHA256 [C030] TLS_ECDHE_RSA_WITH_AES_256_GCM_SHA384 [C02F] TLS_ECDHE_RSA_WITH_AES_128_GCM_SHA256 [C024] TLS_ECDHE_ECDSA_WITH_AES_256_CBC_SHA384 [C023] TLS_ECDHE_ECDSA_WITH_AES_128_CBC_SHA256 [C028] TLS_ECDHE_RSA_WITH_AES_256_CBC_SHA384 [C027] TLS_ECDHE_RSA_WITH_AES_128_CBC_SHA256 [C00A] TLS1_CK_ECDHE_ECDSA_WITH_AES_256_CBC_SHA [C009] TLS1_CK_ECDHE_ECDSA_WITH_AES_128_CBC_SHA [C014] TLS1_CK_ECDHE_RSA_WITH_AES_256_CBC_SHA [C013] TLS1_CK_ECDHE_RSA_WITH_AES_128_CBC_SHA [009D] TLS_RSA_WITH_AES_256_GCM_SHA384 [009C] TLS_RSA_WITH_AES_128_GCM_SHA256 [003D] TLS_RSA_WITH_AES_256_CBC_SHA256 [003C] TLS_RSA_WITH_AES_128_CBC_SHA256 [0035] TLS_RSA_AES_256_SHA [002F] TLS_RSA_AES_128_SHA [000A] SSL_RSA_WITH_3DES_EDE_SHA
Compression: [00] NO_COMPRESSION
The list of ciphers sent by IE is very different from Firefox's. Presumably the server connects to IE using one of the ciphers that isn't on Firefox's list. That's all I can say at this point.
Hello, Considering my last reply You can try to disable MD5 and re-enable SHA Let's me know if work !
Moambuepyre
My last reply is wrong Sorry!
Here is server hello from IE11 / Fiddler:
HTTP/1.0 200 Connection Established FiddlerGateway: Direct StartTime: 13:55:35.564 Connection: close
This is a CONNECT tunnel, through which encrypted HTTPS traffic flows. To view the encrypted sessions inside this tunnel, enable the Tools > Options > HTTPS > Decrypt HTTPS traffic option.
A SSLv3-compatible ServerHello handshake was found. Fiddler extracted the parameters below.
Version: 3.3 (TLS/1.2) SessionID: D3 31 00 00 A7 9B 1A 22 5F 00 30 20 63 12 08 46 FF CF 66 55 C2 25 23 B5 E0 99 FC C2 AE D3 F7 1D Random: 5B B6 62 27 18 8C AB 92 12 5F F4 43 7B 9D C8 91 59 4A 2B 0F E7 F1 95 F6 E5 75 29 84 77 A5 96 F9 Cipher: TLS_RSA_WITH_AES_256_GCM_SHA384 [0x009D] CompressionSuite: NO_COMPRESSION [0x00] Extensions: status_request (OCSP-stapling) empty extended_master_secret empty renegotiation_info 00
> Here is server hello from IE11 / Fiddler: ... > TLS_RSA_WITH_AES_256_GCM_SHA384
That's not one of the ones Firefox supports when I check on
https://www.ssllabs.com/ssltest/viewMyClient.html
Maybe this is a limitation of IIS or your version of Windows Server?
How do you map the ssl labs cipher suites to Nartac Ciphers?
There must be a way to generate the ciphers in a list format similar to what you see in Client Hello. My knowledge of IIS and Windows Server is limited, however.