The certificate is not trusted because no issuer chain was provided
I have a problem accessing an https website with Firefox (26.0), but have no problems accessing it with either Chrome or IE. The particular URL deep links into a message forum.
https://www.lotro.com/forums/showthread.php?535472-Update-12-1-Scaling-Instance-Loot
I get the following error message:
This connection is untrusted You have asked Firefox to connect securely to www.lotro.com, but we can't confirm that your connection is secure. www.lotro.com uses an invalid security certificate. The certificate is not trusted because no issuer chain was provided. (Error code: sec_error_unknown_issuer)
Adding an exception works, but only for this one message thread. The next time I have a different thread we go through the same routine.
OK, I've read the forums a bit: Disabled all Add-ons I'm not running any SSL scanning. Both browser.xul.error_pages.enabled and browser.xul.error_pages.expert_bad_cert are set to True. Certificate dates are fine as is my clock/date. I've deleted cert8.db
When it does load rather than getting a lock I get an exclamation point and a mouseover says Website does not supply identify information.
When I tell Firefox to get the certificate I get:
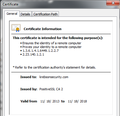
Certificate Status: This site attempts to identify itself with invalid information. Unknown Identity Certificate is not trusted, because it hasn't been verified by a recognized authority using a secure signature.
When I view the certificate I find: Issued To Common Name (CN) *.lotro.com Organization (O) The Saul Zaentz Company Organizational Unit (OU) Secure LInk SSL Wirecard Issued By CN Network Solutions Certificate Authority O Network Solutions L.L.C. OU <Not Part of Certificate> Validity Issued on 1/3/2012 Expires on 1/17/2016
Under Details > Extensions I find Certificate Basic Constraints: Critical, Is not a Certificate Authority.
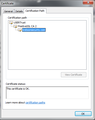
The security trust chain looks like this:
USERTrust
UTN-USER-First-Hardware Network Solutions Certificate Authority *.lotro.com
Все ответы (20)
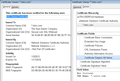
It sounds like you are getting good certificate, or at least the same one I'm getting (first screen shot). Can you check whether you have an entry for "UTN-USER-First-Hardware" in your Authorities tab?
orange Firefox button (or Tools menu) > Options > Advanced > Certificates mini-tab > "View Certificates" button
On the Authorities tab, toward the bottom under The USERTRUST Network, can you find "UTN-USER-First-Hardware"? (second screen shot)
Forgot the screen shots. Here they are:
Regarding the warning icon in the address bar, I get that as well. It indicates that there is some non-secure "passive" content in the page, like images. For forums, I wouldn't be too concerned about that.
The reference to identify information is there for all regular SSL certificates. Only EV SSL certificates (green lock) can verify identity, because the issuer requires some proof of identity for the customer before issuing it.
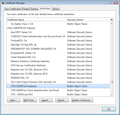
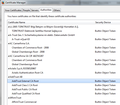
I went in and looked at my Authorities tab and DO have The USERTRUST Network and UTN-USER-First-Hardware. I also have Network Solutions L.L.C and Network Solutions Certificate Authority.
I deleted UTN-USER-First-Hardware and went to http://www.tbs-certificates.com/FAQ/en/42.html and imported the certificate. But when I try I'm told This certificate is already installed as a certificate authority. :( It is back in my Authorities tab is it the new one or not? I didn't exit and reload firefox while doing this.
While searching for UTN-USER-First-Hardware I saw a few stories about some bad certificates issued back in 2011 (addons.mozilla.com and the like). Was their certificate revoked?
Изменено
Hi Paul5358, the story of the fraudulent 2011 certificates is an interesting story, and in the end, the known bad certificates were blocked in two ways (hardcoded in Firefox, and when Firefox checks certificate validity, reporting that they are invalid). The certificate used for LOTRO is not one of those bad certificates.
Because Comodo is a leading low-cost provider of SSL certificates, distrusting the UTN-USER-First-Hardware certificate used to sign the fraudulent certificate also will distrust thousands of legitimate certificates used around the web. In a post-mortem article, that was estimated to impact 205,000 sites (13% of all secure sites) whose SSL certs ultimately are signed by that certificate. So I don't think it's practical to distrust it (you can't actually delete the certificate, as you discovered, but you can distrust it).
But this leaves the mystery of why you get an SSL error when visiting the forum. Could there be some software that is intercepting your secure connections and bungling the certificates, such as security/filtering software or malware? Or is Firefox connecting through a dysfunctional proxy/privacy service? One place to check for indirect connections is the Options dialog.
orange Firefox button (or Tools menu) > Options > Advanced > Network mini-tab > "Settings" button
The default setting is "Use system proxy settings", which should piggyback on the settings in Internet Explorer. You also could try "No proxy".
Изменено
I checked Configure Proxies to Access the Internet. And found it was set to; "Use system proxy settings". I changed it to "No proxy", saved it and reloaded. No joy :(
Leaving the proxy settings at No, I disabled all of the Add-ons and rebooted into Safe Boot with Network via MSConfig to eliminate the chance that some loaded and forgotten program was doing something. Still the connection is untrusted.
Because I use LassPass and Xmarks, I'm not adverse to blowing away Firefox and reloading it. If I can remove it and not leave any crumbs behind.
Изменено
You can manipulate the two aspects of the program separately:
(1) Settings - to test with clean settings, you can create a new profile; let's hold that thought.
(2) Program - sometimes program files become corrupted, which usually can be repaired by re-running the full installer. However, if other software has dropped files into Firefox's program folder, those won't be replaced or removed. This is by design so you don't lose plugins dropped there, but could be the source of the problem. To address that situation, you can rename the Firefox folder and then reinstall.
Download the installer for your preferred language from this page:
https://www.mozilla.org/en-US/firefox/all/
After exiting Firefox, rename the program folder to something like OldFox.
On 64-bit Windows, it's:
C:\Program Files (x86)\Mozilla Firefox
On 32-bit Windows, it's:
C:\Program Files\Mozilla Firefox
Then run the installer. It should find your existing personal data automatically.
Any improvement?
To complete the thought in the previous post, here's the two-minute new profile experiment:
Create a new Firefox profile
A new profile will have your system-installed plugins (e.g., Flash) and extensions (e.g., security suite toolbars), but no themes, other extensions, or other customizations. It also should have completely fresh settings databases and a fresh cache folder.
Exit Firefox and start up in the Profile Manager using Start > search box (or Run):
firefox.exe -P
Any time you want to switch profiles, exit Firefox and return to this dialog.
You'll click the Create Profile button. I recommend using the default location suggested, and to avoid data loss, not re-using any existing folder. Then start Firefox in the new profile you created.
Does Firefox accept the certificate when you access the site in the new profile?
When returning to the Profile Manager, you might be tempted to use the Delete Profile button. But... it's a bit too easy to accidentally delete your "real" profile, so I recommend resisting the temptation. If you do want to clean up later, I suggest making a backup of all your profiles first in case something were to go wrong.
With regards to the fraudulent certificates ... if a major root CA were forced to give a root certificate so some ... agency. Short of scrapping the whole chain of trust concept, is there anything that can be done? Seems like the weakest link is very weak.
I don't want to derail my own thread, but I'm sure this has been a topic of discussion. Perhaps you could point me in the right direction to do some reading.
Изменено
I renamed C:\Program Files (x86)\Mozilla Firefox as Mozilla Firefox Old and ran Firefox Setup 26.0. Same results.
I'll try the profile next.
I created a new profile and a couple of things didn't work as expected. It took my new name but the only option highlighted was to select a folder. I skipped that and selected Next and things completed. But when I launched Firefox none of my addons were present.
Oh, by the way, lotro is still untrusted.
Hi Paul5358, it's normal to find that the new profile is mostly blank. That's the point of the test, actually, to see how Firefox would run if you had removed all your settings.
So I think you've ruled out both the program files side and the settings side.
There might be some registry settings that we've left in place through all this, but hopefully someone else will have some insight on the problem since I'm out of time.
Check the date and time in the clock on your computer: (double) click the clock icon on the Windows Taskbar.
Within a second, it looks like my internal time is correct 6:58:10 PM Sunday, December 22, 2013.
Try to create a new profile as a test to check if your current profile is causing the problems.
See "Creating a profile":
- https://support.mozilla.org/kb/profile-manager-create-and-remove-firefox-profiles
- http://kb.mozillazine.org/Standard_diagnostic_-_Firefox#Profile_issues
If the new profile works then you can transfer some files from an existing profile to the new profile, but be cautious not to copy corrupted files to avoid carrying over the problem.
I've found another site that gives my Firefox instillation the same fits;
krebsonsecurity.com uses an invalid security certificate. The certificate is not trusted because no issuer chain was provided. (Error code: sec_error_unknown_issuer)
The chain of trust is:
USERTrust
PositiveSSL CA 2
krebsonsecurity.com
I assume that USERTrust in kreb's certificate is the same or related to The USERTRUST Network used in lotro's certificate.
Is there something silly I could have done back in ... 2011 when Comodo / UTN-USER-First-Hardware certificate signed those fraudulent certificates? Was there some "temporary" fix I could have put in the registry or hosts file or something?
Изменено
I created a new profile, and the problem persists.
I tried the kreb's site again and noticed that if I just type in krebsonsecurity.com and hit enter Firefox works as expected. The problem comes when I enter https://krebsonsecurity.com/ and I found that is also true of the lotro site. Https is how the lotro link is listed in Google, but perhaps these sites don't support secure connections?
Изменено
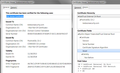
Hi Paul5358, I get a different authority signing the cert on krebsonsecurity than you do. Screen shot attached.
Your last reply raises a good point: if you do not need to use HTTPS to browse the site, because privacy is not a high concern, then it certainly is simpler not to.
But it still should work as designed... I'm not aware of any way to block an authority's certificates from outside of Firefox, and any changes you made inside of Firefox usually would have been limited to your old profile.
Изменено
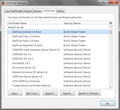
The krebs certification path I listed was how Chrome displays it (attached). I didn't try Firefox the first time, but I did just now and it displays like yours. My Authorities is much smaller than yours though. Under AddTrust AB I only have the 4 Builtin Object Tokens.