Urgent Fire Fox Update Notice
I keep getting a screen popping up that says "Urgent Firefox Update". My protection software is blocking it, saying it's a Trojan. When I go to Mozilla, it says my Firefox is up to date. Is there an Urget Update or not?
Valitud lahendus
Hi
We are aware of this issue are are working to resolve it. From what you are saying this is almost certainly malware.
Firefox will always update from within the browser and not from a random web page. If you ever unsure of whether you are using the most recent version, this page will walk you through how to check.
Comment added by a forum moderator Please also see our help article
If you do see one of these fake updates please as a reply to this thread post the web address of the fake orange page and if possible the address of the genuine website it appears to have come from - the back arrow on the address bar of the orange page may sometimes help find that.
Loe vastust kontekstis 👍 236All Replies (20)
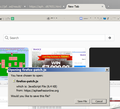
Firefox opens homepage yahoo.com but another tab opens with FF color and logo stating to download this Firefox Update. https://oophig-tools.com/3571824514203/0a3f0fb3b55733687efd3c163838392c/b65d0c99f71438740adbe2e913464f86.html I have checked the startup page which is only Yahoo.com and I checked addons and plugins which has only the correct plugins listed. I am using Avast with Avast FF addon and Avast states the website is legitimate (LOL). The download file is a JS file and I did not download it. What is funny is the web address I listed does not load if I enter the web address manually.
PS did U notice the main URL of the two above is the same (same day) but after the slash they differ?
Thank you both for sharing what you have. I hope you reported the web page (orange screen) so as to help others NOT get there TODAY. I did 4 this one, just in case. You get a gold star for trying, but I warn you, give it up (politely). Why? I have spent countless hours to no avail. The warning is for how compelling the search can become for you as it did for me.
If you read alll 9 pages of this thread, you will read that the web site, or some machine in between you and any number of other machines contacted, knows you went there today and you are not eligible to get another chance to see the orange screen until tomorrow when the URL has changed to a newly registered one. I did find a semi-related event on one of those click-bate sites. It used some cookie value and produces a pop-up screen but only for a few minutes. I saved the code (view source) on my machine. When the date changes, I can get it again. But I haven't today. In the click-bait case, the ame code is inside every web page. For the orange screen, no one has seen the actual offending/testing code which makes the 'left turn' to the orange screen server, although the event has always been connected to advertisements. (read the post where any company suspected of involvement has been less than helpful.)
If you've played with 'view source', I do not know if it takes it from inside your machine or goes and fetches a new copy from the server - which may not be the same was what was executed on your machine the first time.
The evolution of web sites is making things harder. Rotating ads, dozens to more than 100 URL's visited just to produce one page on your screen.
Muudetud
I've been getting it a couple times the past week or two. Both times it goes to the same domain.
This time it's:
Is this through a hacked webpage advertisement? I was just on yahoo's website and it did it. It was white-listed in disconnect plugin. So black listing yahoo, but things may not work then?
But the history shows the site prior was http://www.fooducate.com/app#!page=post&id=57A3388B-3952-0BED-46E9-BD36BE6CE508
Muudetud
That link brought up the urgent patch tab yesterday. This is a screenshot of today, just popped up saying I had chosen to open. Here is the link for today's more aggressive occurrence: https://aphaefrasionline.org/541803105357/309f2183a4db1ea93e5dfeb4b89a0ec6/b44fc7e3104d8ee6c1962f7f58d67651.html
Muudetud
I have been checking the whois on this thing and almost 100% of them are registered with publicdomainregistry.com. I have sent numerous complaints but they keep registering the domains. Maybe Mozilla can jump in and put some pressure on them.
Do not waste your time with emailing their abuse or compliance departments (ie, filling out their form) because it is a waste of your time. Their purpose is to make money and do not care otherwise. They will de-register the URL, which takes hours/days to migrate across the Internet, which will stop some people from reaching the "orange screen", and do not charge for the registration (free for 4 days or less.) Public Domain Registry was advise of one name/customer who registered the orange screen DAILY, and they replied to me they would be dealing with the issue, but they NEVER did. I was the fool for trying. They will not release any info about their clients. I will send you their email "lip service" if you want, but PDR does not care and also do not follow their own legal document on requiring real info, so the name/address/phone shown on a whois screen might be a vacant lot. I considered other US agencies, but they seem to be "did you lose any money." One guy claimed contacting the FBI, but seriously ... You'll find more about PDR on this support forum and the vast efforts attempted so far, but thanks for trying. Post Script - the web sites which you visited B4 getting to the orange screen are also either non-helpful or want a reproducible example.
I am still amazed that Mozilla cannot fix FF. The websites that get hacked are random and I don't even think they know that the Orange Screen of Death (OSD) even exists. The last time I got the download request, I did not get the OSD.
I always run whois on the website and every time it comes up with a different location, name and phone number. Every time I have contacted PDR, they have removed the website within 24 hours, but I doubt that PDR knows who they are registering and that is the major problem. I have contacted ICANN about the situation, but they don't even respond.
We are sitting out here is this big world all alone... Where are you Mozilla???
It is not a exploit or security issue with the Firefox browser. It is due to a form of malvertising on what may be legit websites. The scammers behind this are also targeting Google Chrome users on Windows and more recently I discovered they may be starting to put out fake Adobe Flash Player update pages.
In the past the fake Firefox download or update sites would stay up until taken down after a time (helped take a dozen+ down myself). The sites used for this particular scam pages are more disposable as they are registered, used for a day or so and then not used again.
No Firefox user on Mac OSX or Linux has reported these fake urgent Firefox update pages, only on Windows. Perhaps for a couple reasons, more likely to encounter less experienced users who fall for it and because the .js file and what it tries to install on OS may not work on OSX and Linux anyways.
https://support.mozilla.org/en-US/kb/i-found-fake-firefox-update
Muudetud
FF and google chrome are the only browsers that have this issue. Even though you have to be aware to not download things you don't know what they are, there is still a problem with Mozilla's code that it can be exploited or IE would be having the same problem.
Nothing to do with any Mozilla code as to why Firefox (and Chrome) browser users are getting fake urgent update sites. The malvertising Ad's see you are using a Fx on Windows based on useragents and serve you the fake sites if they target you. As I said I have seen no Fx user using Mac OSX or Linux reporting any of these fake urgent Firefox updates sites which shows they are only targeting Fx UA's on Windows.
Muudetud
Don't know what "Fx" or "UA" is, but I do know that only Mozilla is being attacked. I have been on sites that I know and had the popup emerge after I have been setting there for some time - never with IE.
Fx is the proper abbreviation for Firefox ever since the browser was named Firefox as of version 0.8 back on February 9, 2004 (not FF as many newer users think) and UA is the common abbreviation for the useragent word mentioned in post. Think about it, FX and Firefox mentioned in same post ;)
Development of IE is essentially discontinued now with IE 11 supported with more security than older versions of IE. Edge has replaced IE as default browser on Windows 10.
So the scammers may not care to target IE and they would only be targeting Windows 10 users with Edge.
As said the scammers have even made up a fake Adobe Flash Player download page serving a FlashPlayer.js on a same disposable site that was used for a fake urgent Firefox update, however I have only seen just the one instance so far.
Muudetud
Never seen "Fx" used before.
I just used IE as an example, there are several others that are not targeted, it is simple enough to test for any browser. Fake sites cannot carry the same name as a target site, so there has to be another reason because I always check the site name. The only time I see the ad is through some made up name "after" landing on a reputable site.
It should be simple for Mozilla to block any site that refers to a site that has the download connected to it by just looking at the text on the page. Apparently the download is targeted to Fx code only since it is written in ever day text rather than compiled. I personally wrote code in ver 18 to launch as executable that they said could not be done. Mozilla is extremely vulnerable to be hacked. Another person wrote code to allow the running of unsigned extensions that I use for newer versions that try to block them.
Muudetud
Interesting concept that FF (Fx?) might test for downloadable code. I think you should run with that idea for awhile. I wanted to recap some previous postings about web sites containing advertising, and the source code (view-source) of the javascript where a link is made to a page/web advertiser, which, using google analysis tools, determines what browser U run, what country U R in, what color underwear U wear and your email address (found in source code!) then goes to an advertising site, a different URL then one might think. And Javascript programs can call/run/link to other places before ever returning to the main web page. Or should I say these processes run in the background while the main page is still being loaded.
Due you your posting, I went looking at an IE log and found links to ML314.com which has some interesting text on their main page ("Embedded content loaded from third-party domains."). I also got a hit with a search engine, yielding http://www.dshield.org/forums/diary/False+Positive+or+Not+Difficult+to+Analyze+Javascript/18593/ which is a blog with a user comment of: I would agree that this is almost certainly advertising of some sort, but with my experience of malware infested ad servers, ....
Note those last 3 words. With all the layers, with legit sites advising a user that 'flash is out of date" which may be true, and the power of programming, the feature of corrupting a personal computer was warned back in 2013.
Network owners do not police their customers. Maybe the infections are intentional. I am not aware of what the FFupdate actually does, or will do. One site I found which I thought might be involved was getting 78K hits per day, starting from zero, about the time the FF first began. Why only 78,000? At least FF which gives the orange screen and has the pop-up "download" option screen does not automatically load the phony-update code. For now.
Can Mozilla fix or prevent this? So far no volunteer has accepted trying. This is not a MicroSoft/Google funded company. Maybe there is reason that Microsoft products were excluded from phony-updates (IE updates come during windows-updates, IF windows-updates are still runable on a persons machine.)
I haven't gotten into FF code, just a lot of web site souce. But with the evolving power and complexity of software (and bad programming), I am reminded of Howard Marks who allowed an entry system to accept someone ordering "Bottles of typewriter ribbons."
new event 12/28 3 AM EST.
the popup for firefox-patch.js is to be from the same (major part of) URL.
2 cookies, expire 10 minutes after OS displayed.
Was viewing multiple pages from oddnews of yahoo. At the time, clicking through the 6 photos of the lost teddy bear at airport.
But note that the popups typically have a delay/sleep command, 6 to 30 seconds, or more. So which page and ad caused this?
doing a 'page back' I go to view-source:https://www.yahoo.com/news/teddy-bear-takes-detroit-airport-adventure-being-found-165438396.html
but do not ignore that JS programs can destroy history, hence there was probably some intermediate page starting from the yahoo advertisement.
I went to http://cqcounter.com/whois/ and saw a new (to me) user in Hackensack NJ, but the typical host in Miami for ReliableSite.Net LLC
mapping software of the owners address found no match. Phony name/address info accepted by PDR? I reported the site using the FF , help, 'report deceptive site' so hopefully less people with get the orange screen TODAY. Perhaps there is a better site to report maware for faster global blocking of site. ??
Muudetud
I had thought about the ad scenario which seem to make since, this seems to be the only way that this could happen.
I have been blocking ads through windows "Host" file and will continue to do so until (maybe) this thing stops and possibly find an ad and its' source.
There is still an underlying issue with the malware itself and its' ability to infect through FF/Fx.
was viewing https://www.yahoo.com/news/odd/ and the teddy bear story again starting at 3AM Eastern time 12/29 and sure enough, new OS, from leejopr-canada.com because today is a new day. Was running processExplorer to see if anything abnormal therein, but stopped it just before actual 04:01 orangescreen. Tomorrow I will skip the teddybear.
It's happened a few times now and at the beginning, I figured it was legit. Still, the "patch" was delivered in what seemed to be an odd an unusual manner. About the fourth time, I began to wonder, and especially when it wanted to replace a "patch" already there, then I googled for the problem and found this site. So just this morning it happened again.
I was on this Yahoo news article: https://www.yahoo.com/news/m/b9356e26-b9e0-30ef-a076-06a4c62f2f6e/panel-delays-decision-on.html
And the URL of the "patch download" screen was this (I'd never even looked at the URL address before, assuming the notification was legit): https://usaemeventualmillionaire.com/613550806155/3ca9d6a1bb5e0750725f88cc7b6cb834/6596f24d8b15e1067e77c32dd32f4189.html
jujubee2259 said
It's happened a few times now and at the beginning, I figured it was legit. Still, the "patch" was delivered in what seemed to be an odd an unusual manner. About the fourth time, I began to wonder, and especially when it wanted to replace a "patch" already there, And the URL of the "patch download" screen was this (I'd never even looked at the URL address before, assuming the notification was legit):
The orange background and large Firefox icon was done by the scammers to try and make the page look legit and to distract less experienced Windows and or Firefox users from that fact it was on some random weird name url and not on a *.mozilla.org url.
I have the "Urgent Update" Malware issue also. I tried Uninstalling Firefox and reinstalling it. However, it still comes back. FYI