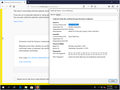
Firefox does not trust any root CA's, including the one used by Mozilla.org
Technical details here... It's a windows 10 box that's had all the recent updates applied. This is a fresh install of Mozilla Firefox Quantum, version 66.0.2, 64-bit. The time in the screen shot may appear to be off, but the box is currently in India so it is actually correct.
We applied this update to our environment and ended up with an issue where Firefox refuses to accept any website. We've tried hitting mozilla.org, google.com, yahoo.com, cnn.com, apple.com, just to name a few.
We found a bandaid for the issue. It was found on what appear to be unrelated issues, but it works for the moment. We toggle the "security.enterprise_roots.enabled" property to "true" in the "about:config" portion of Firefox. I found a few tidbits on that property here: https://mike.kaply.com/2016/09/01/upcoming-changes-to-root-certificates-in-firefox-on-windows/
However, that article only references Root CA's that are setup on the OS, not within Firefox itself. Does this mean that a freshly installed version of Firefox no longer has a Root CA store and it can't be bothered to trust the OS's Root CA store either? If so, why? It makes the browser unusable. Predictably enough, it's all the end user's favorite browser and it performs better than the others we have available to them.
The enterprise_roots option is a bandaid in our environment. As soon as people log out, their desktop is reset to a default state. What all is involved in fixing this so we can get business back to normal?
Seçilen çözüm
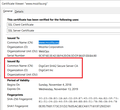
Hi, does "Quick Web Proxy" -- the issuer of the certificate you see -- ring a bell? In other words, is that an intentional man in the middle, or a suspicious interception?
(I'm attaching a screen capture of the normal certificate.)
Bu yanıtı konu içinde okuyun 👍 0Tüm Yanıtlar (3)
Apparently, our screen shot didn't upload last time. Trying again...
Seçilen çözüm
Hi, does "Quick Web Proxy" -- the issuer of the certificate you see -- ring a bell? In other words, is that an intentional man in the middle, or a suspicious interception?
(I'm attaching a screen capture of the normal certificate.)
Interesting. I do believe I missed that detail. I will look farther into this with the rest of our team. Thank you!